Benefits of OCM
On this page
Software development is complex. Most organizations struggle with fragmented tools, complicated workflows, and the challenge of managing software across different environments - cloud, on-premises, hybrid, and even air-gapped networks.
Traditional approaches lead to:
- Complicated, custom CI/CD pipelines
- Inconsistent software delivery
- Difficulty tracking and securing software components
- Lack of a standard way to describe software and its artifacts
Requirements Towards a Modern Software Component Model
Community-First Approach
A truly modern software component model cannot live in isolation. It needs an active, diverse community to grow, adapt, and remain relevant. Open source projects invite users and maintainers to propose ideas, report issues, and deliver improvements. Lowering entry barriers nurtures diverse perspectives, accelerates innovation, and ensures real-world feedback shapes priorities. Continuous collaboration - through design discussions, reviews, and documentation — builds trust and fosters adoption across industries. In this way, the community itself becomes the guarantor of quality, relevance, and long-term sustainability.
Immutable and Unique Component Identity
A crucial requirement is the ability to assign an immutable and globally unique Component Identity to each software component. This identifier acts as a “correlation ID,” allowing all lifecycle management processes, such as security compliance and vulnerability scanning, to correlate their outputs to a single, identifiable software component.
Artifact Descriptions with Location Information
The model should facilitate the description of all technical artifacts required for deploying a specific version of a software component. This list, termed a “Software Bill of Delivery” (SBoD), outlines only the artifacts needed for successful deployment. Additionally, the description must encompass the technical access location from which each artifact can be retrieved.
Separation of Component Identity and Artifact Location
Organizations often need to:
- Store artifacts in local registries
- Work in environments with limited or no internet access (air-gapped)
- Move artifacts between different systems and environments
The Component Identity must remain stable across all boundaries and system environments, while the artifact locations should be changeable. The ideal model separates the component identity from its artifact locations, allowing maximum flexibility.
Technology Neutrality
Real-world software environments are messy. A good component model must:
- Support modern containerized applications
- Handle legacy software
- Work across clouds, on-premises, and hybrid infrastructures
Technology-Agnostic and Forward-Thinking Design
The model should:
- Adapt easily to emerging technologies
- Avoid constant rewrites of existing tools and processes
- Stay relevant as software development evolves
- Cover both legacy and modern software
Built-In Security
Automatic capabilities for:
- Signing software components
- Verifying artifact integrity
- Protecting against tampering
- Maintaining trust across changing artifact locations
Collaborative Potential
Enable teams to:
- Easily share and reuse trusted components
- Create a network of verifiable, reusable and high-quality software building blocks
OCM: Solving Software Lifecycle Complexity
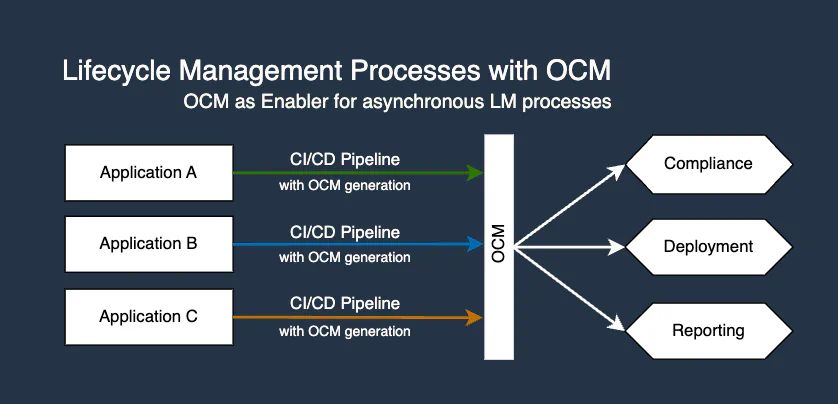
The Open Component Model (OCM) is designed to tackle these challenges head-on. It provides a standardized approach to describing, managing, and sharing software components that brings order to software lifecycle management. By linking additional metadata using OCM’s identities, it facilitates asynchronous handling of various lifecycle management processes, such as compliance checks, security scans, deployments, and more, in a decoupled and streamlined manner.
Community-Driven Governance: OCM’s open governance and transparent contribution workflow empower anyone to asynchronously propose, review, and merge enhancements — keeping its software lifecycles aligned with evolving community needs.
Unique Component Identities: OCM assigns an immutable, globally unique ID to each component, enabling seamless correlation across all lifecycle tools and processes.
Software Bill of Delivery: OCM enables the specification of all artifacts required for delivering a software component. This compilation, termed a “Software Bill of Delivery” (SBoD), lists all artifacts and information how to access them.
Stable IDs, Changing Artifact Locations: OCM separates immutable component IDs from the changeable artifact locations, essential for private and air-gapped environments.
Technology Agnosticism: Being agnostic to implementation technologies like container images, NPM packages or binaries, OCM can handle both cloud-native and legacy apps.
Future-Proof Extensibility: OCM’s extensible design allows simple adaptation to emerging trends without disrupting existing tooling.
Trusted Signatures: Built-in signing and verification ensure artifact integrity even as artifact locations change over time.

OCM creates a “single source of truth” for software artifacts. It streamlines compliance checks, security scans, and deployments by providing a consistent, location-independent way to identify, access, exchange, and verify software components.
By making software component management more transparent, secure, and efficient, OCM helps organizations transform their software delivery from a complicated puzzle into a smooth, manageable process.